
By offering security systems, we block unauthorized access to your IT environment. Attack analysis and threat simulation identify areas that need to be secured. Based on the results, we protect the basis of the program with the help of architecture and secure code viewing. The final stage includes vulnerability assessment and penetration testing.
Due to the increasing number of cybersecurity threats, there is a constant need to monitor and handle incidents. The operational security center identifies risks to the actual attack. After completing the process of identifying and resolving the problem, we perform deterrence actions. Our analysts are working to improve the rules for identifying and intercepting new threats. Implementing a complete data leakage prevention process allows you to analyze your data and identify areas that need protection. Based on this, we develop a strategy against data leakage and implement adequate DLP tools that improve security. Our specialists adjust the notification rules and test them to classify events. The team handles DLP events and quickly detects potential incidents.
The company implements security solutions after a detailed analysis of customer expectations. Our specialists study both the infrastructure and the network to make the security consulting process as effective as possible. By developing an open source infrastructure, we strengthen your cybersecurity. If necessary, we track your products from a security perspective and review key security design points, including source code.
OrderWhen ordering software development, the process will be as follows:
Receiving a task from the customer, discussing technologies and principles of product operation
Software product development based on customer-selected technologies and design.
Testing of the software product for the content of errors and correction of shortcomings.
You can order the development and implementation of the following software products:

Creating a website consists of a series of steps. Our advantage is that we provide a comprehensive approach to creating sites at any stage.
See more
With state-of-the-art tools and technologies, we create applications that can support your business and install on your customers' mobile devices.
See more
Software development includes the creation, design, deployment, and maintenance of computer software for early operating systems.
See more
We develop design concepts. Then the concept is agreed with the customer and finalized according to his needs.
See more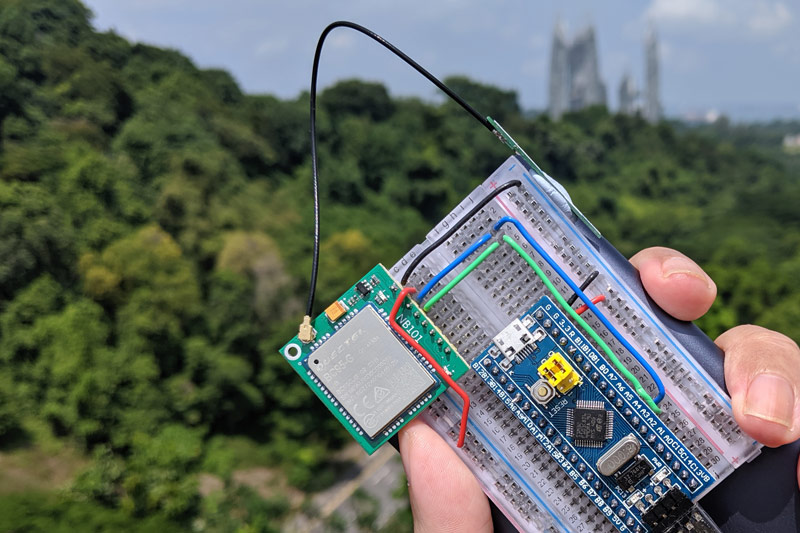
We create software products that are combined with cloud services and IoT devices. We provide server infrastructure, network and security management services.
See more
RPA is a multi-vertical and cross-cutting technology that can automate various processes and tasks regardless of the nature of your business. We can perform the full implementation of robotics or only individual steps.
See more